Google WorkSpace Directory Dump Tool
Google Workspace Directory Extraction Tool :
During a Cloud Red Team Project, as our last objective we were tasked with reviewing the Google Cloud architecture. As a part of enumeration we were checking the user / group relationship and identifying the set of privileges that can be leveraged. The process was tedious and required a manual approach to perform the operations. We came up with a very good approach to automate the process using Google APIs and export a list of :
1. Users
2. Groups (along with relationship)
Think of this in a scenario where there are 1000s of users / groups in GCP environment. The results can then be integrated with neo4j to visual the relationship which will aid further operations.
The things that are required for the user/group dumping operation are :
1. OAuth Credential
2. Organization ID
Steps :
A) Obtain OAuth Credentials from the Google API Console :
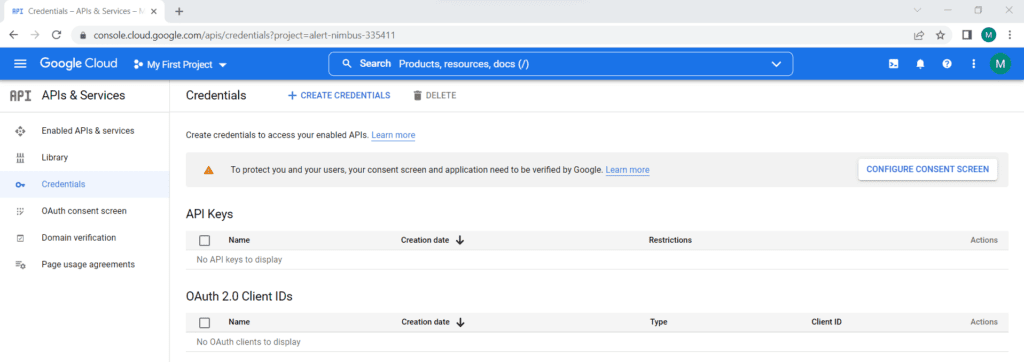
OAuth Credential has a Client ID which is unique and a Client Secret.
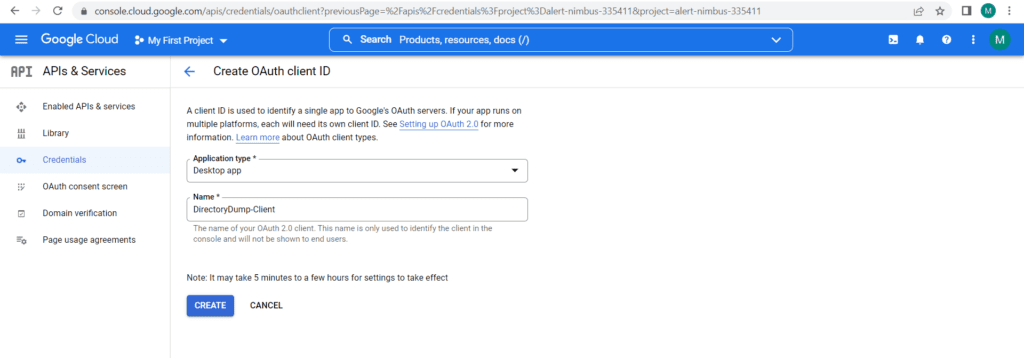
A Client ID is used to identify an application to the Google’s OAuth servers. This can be generated on demand directly from Google Cloud Portal and downloaded in JSON format.
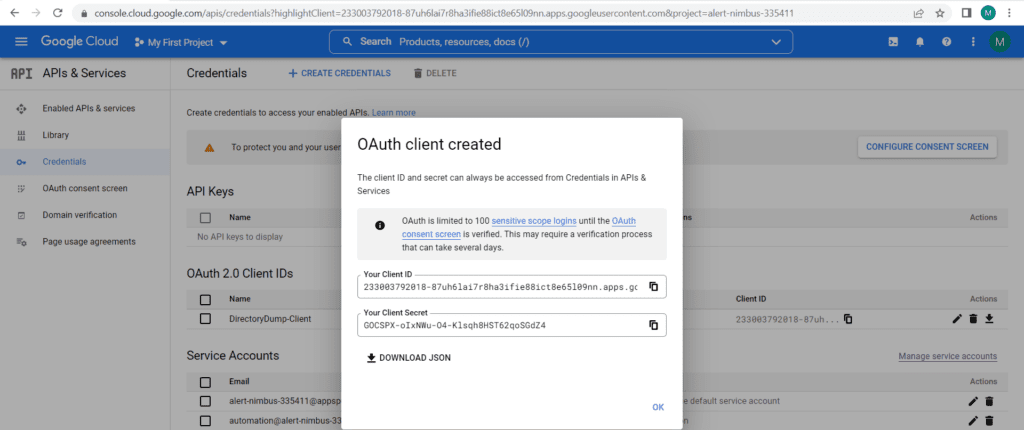
B) The generated JSON file (Client ID & Client Secret) can then be used to obtain the authorization code. Our code will handle all the necessary steps of OAuth 2.0 protocol required for making API calls.
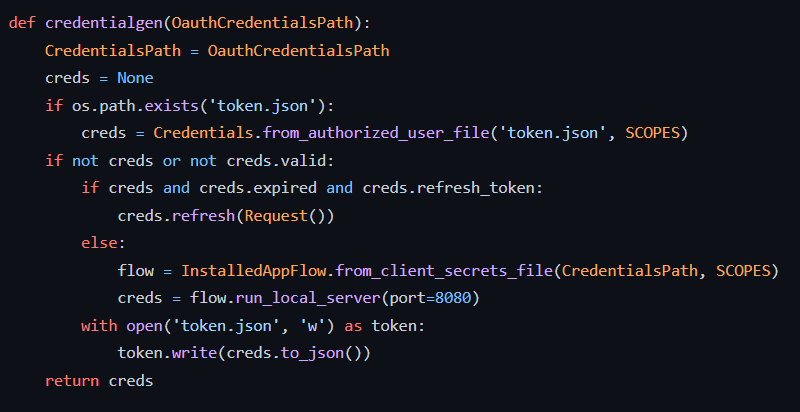
The above code execution will open the default browser where we will be required to provide the permission for the app to access the directory resources.
Scope of the authorization token is already defined in the above list. As clearly visible we have defined the scope of reading the directory resources (user & groups)
The obtained access token can then be used to access the data from the google cloud directory.
C) The Application will require 2 permissions, “Cloud Identity Groups / Members & Emails” & Download GSuite Directory.
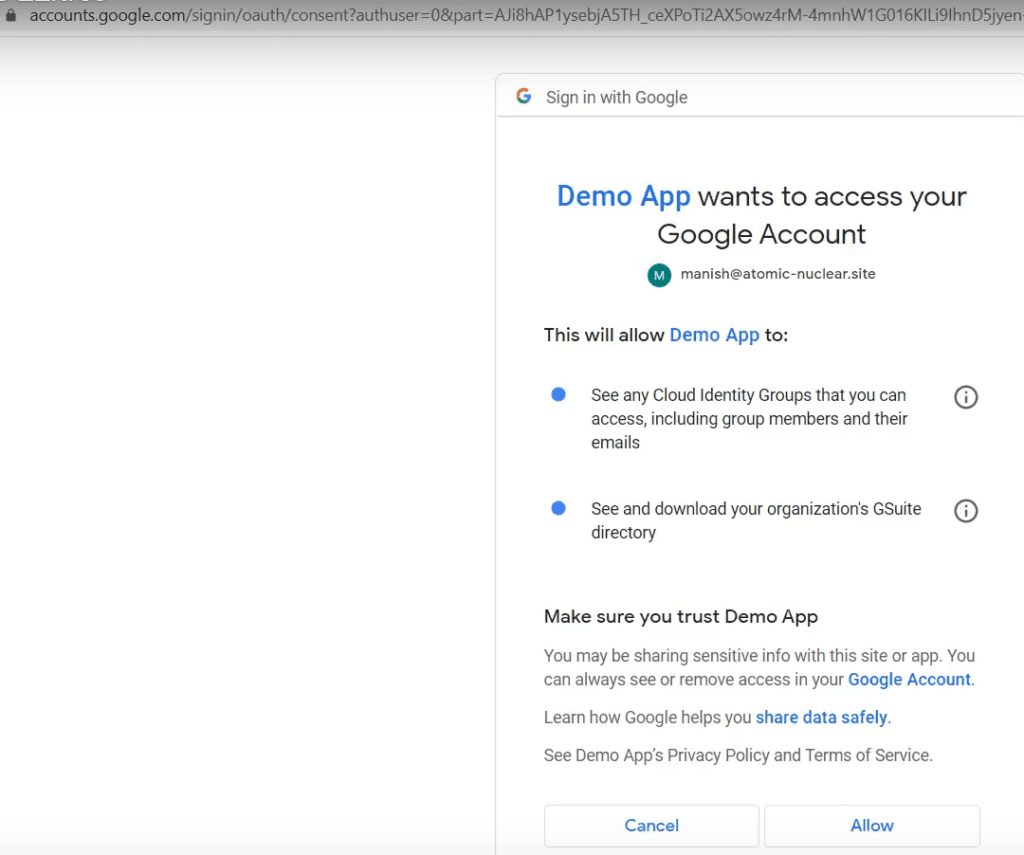
D) Extracting the Google Cloud Directory users & Groups
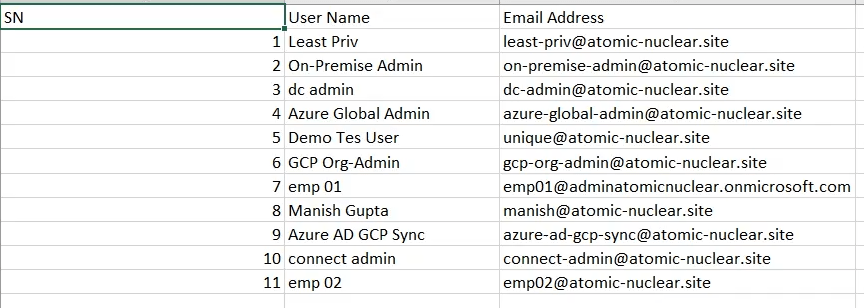
E) The extracted information can be fed to Neo4j a graph database management system to visualize the group membership relationship
The tool eases the process flow of directory user / groups extraction and later utilizing it for visualization. The extracted information can be leveraged to identify the privileged identities and plan ways to compromise them.
Script Link : Google Workspace Dump Tool
We will be documenting various unique findings in our Cloud Red Team Journey here. Till then stay tuned !
Stay connected with news and updates!
Join our mailing list to receive the latest news and updates of cutting-edge cyber security research from our team.
Don’t worry, your information will not be shared.































