The training contents are divided across 4 sections listed below:
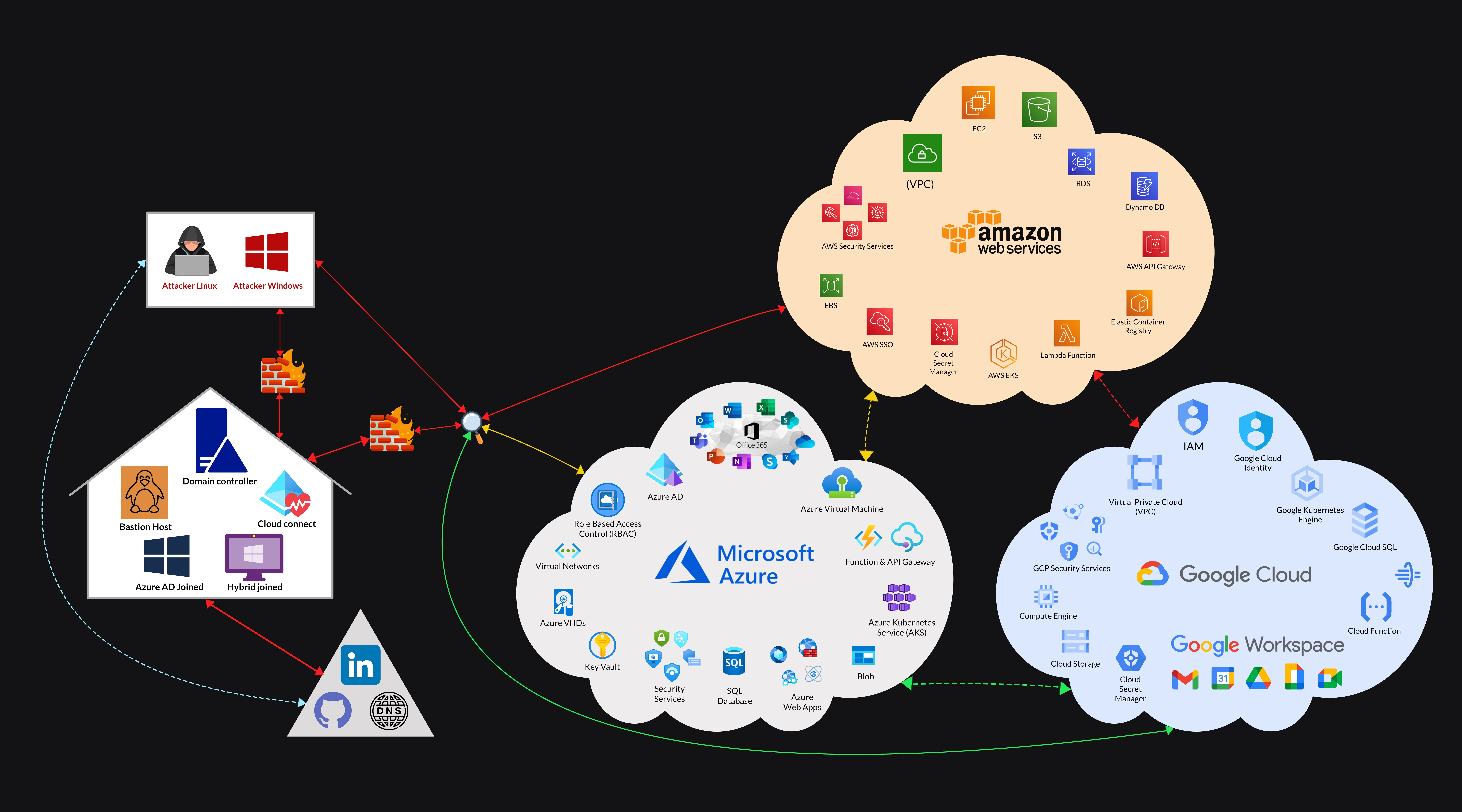
Attacking - AWS Environment
- Enumerating & Designing Attack Surface of AWS Cloud Services
- Exploit Lambda Function for Persistence & Privilege Escalation
- Pivoting & Lateral Movement using AWS VPC Service
- Post-Exploitation by abusing mis-configured AWS Services
- Data Exfiltration from S3, RDS, STS & Secret Manager etc
Attacking - Azure Environment
- Enumerating & Designing Attack Surface of Azure Cloud Services
- Pivoting Azure Control Plane to the Date Plane
- Stealth Persistence Access of Azure account by Service Principal
- Privilege Escalation by abusing mis-configured RBAC
- Mis-use Azure Authentication Methods [PHS, PTA, Federation].
Attacking - GCP Environment
- Enumerating & Designing Attack Surface of GCP Services
- Enumerating & Exploiting Google Kubernetes Services
- Post-Exploitation by abusing mis-configured GCP Services
- Privilege Escalation by exploiting mis-configured OAuth & IAM
- Persistence Access by Temporary/ Permanent Access Token
Attacking - Hybrid Multi-Cloud Environment
- Lateral movement from one Cloud to another Cloud Platform
- Enumerate & exploit widely used SaaS Services (O365, G-Suite)
- Exploit Trusted Relationship for expanding the access
- Pivoting from On-premise to Cloud environment & vice-versa
- Use Manual/Open-Source Tools for Offensive Operations
CYBER RANGE LABS HIGHLIGHTS
- Hybrid Multi Cloud Enterprise Simulation Lab
- CHMRTS Digital Certificate + Badge
- Red Teaming in On-Prem, AWS, Azure & GCP
- Study Materials : 500+ Pages PDF
- Recorded Training Videos with technical support
- Mapped with Enterprise MITRE Cloud TTPs
Pre-requisites
Following are the requirements:
- Fair Knowledge of Networking and Web Technology
- Familiarity with command line interface
- Familiarity with virtualization technologies
- Basics of Penetration testing methodology
- An Open mind 😊
- No prior Cloud knowledge is required.
Target Audience
Targeted Audience may include the following group of people:
- Penetration Testers / Red Teams
- Cloud Security Professionals
- Cloud Architects
- SOC analysts
- Threat Hunting Team
- Anyone who is interested in strengthening their offensive capabilities in multi-Cloud environment
Premium Version
$699
Top Features:
- 500+ pages PDF
- 12 Hrs+ Training Recorded Videos
- 30 days Practise Lab Access + 1 Year technical support
- 2 Exam Attempts
- Verified Accredible Certificate + badge
Note: If you want to extend the days for lab access please drop a mail at:
[email protected]
![Hybrid Multi-Cloud Red Team Specialist [CHMRTS]](https://cyberwarfare.live/wp-content/uploads/2025/11/CHMRTS.webp)





































